Introduction
UK businesses in 2024 face a multifaceted cyber threat landscape, ranging from ransomware and phishing attacks to intricate supply chain vulnerabilities and emerging AI-driven threats. The interconnectedness of global markets and the proliferation of remote work models further amplify these risks, requiring a heightened focus on securing networks, data, and devices. Compliance with stringent data protection laws like GDPR, coupled with evolving regulatory frameworks, underscores the mandatory nature of robust cybersecurity measures.
Moreover, customer trust and brand credibility hinge on a company's ability to safeguard sensitive data and maintain operational continuity amidst cyber adversities. The ripple effects of a cyber breach transcend immediate financial losses, often impacting market standing, customer loyalty, and even legal ramifications. Consequently, in 2024, investing in cybersecurity isn't merely an option but an indispensable strategic imperative for UK businesses to thrive in an increasingly digital-centric landscape.
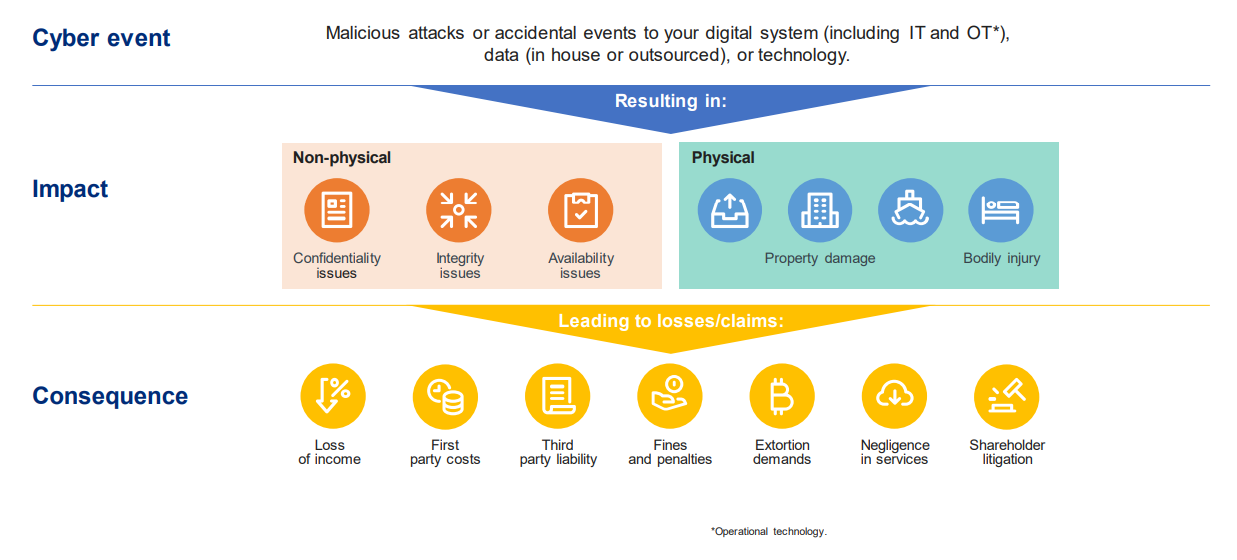
Understand the impact and consequence of a cyber event
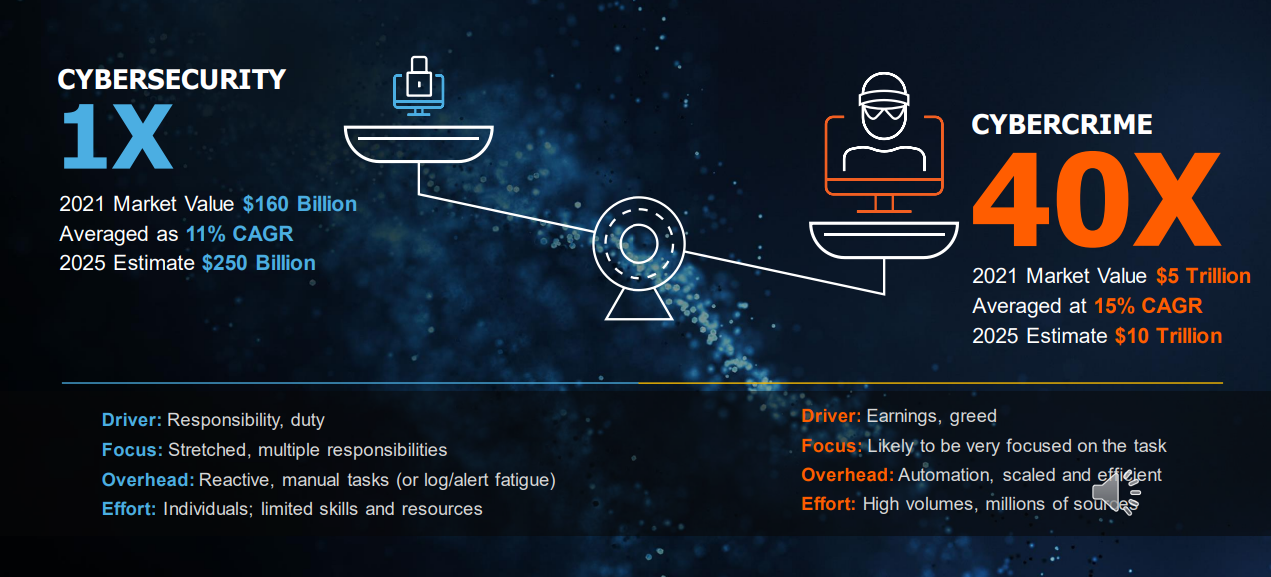
Cybercrime is now the third largest economy behind America and China
Current Cyber Threat Landscape in the UK
Using the results from this Cyber Security Breaches Survey, we estimate that:
UK businesses have experienced approximately
 2.39 million cyber crimes of all types
and approximately 70,000 non-phishing cyber crimes in the last 12 months.
2.39 million cyber crimes of all types
and approximately 70,000 non-phishing cyber crimes in the last 12 months.
 UK charities have experienced approximately 785,000 cyber crimes of all types in the last 12 months.
UK charities have experienced approximately 785,000 cyber crimes of all types in the last 12 months.
Looking across all the different types of cyber crime, it is estimated that  11% of businesses and 8% of charities have been the victim of at least one cyber crime in the last 12 months. This accounts for approximately 159,000 businesses and 15,000 registered charities.
11% of businesses and 8% of charities have been the victim of at least one cyber crime in the last 12 months. This accounts for approximately 159,000 businesses and 15,000 registered charities.
Looked at another way, among the 32% businesses and 24% of charities identifying any cyber security breaches or attacks, around a third (34% for businesses and 32% for charities) ended up being victims of cyber crime.
Cybersecurity: The numbers
Breach frequency
73%
of businesses do not have a business continuity plan that covers cybersecurity
View Source
71%
of UK businesses say cybersecurity is a high priority for their senior managers but aren’t doing anything about it
View Source
Breach Costs
$302,000
the anticipated cost per second of Cybercriminal activities to organisations
View Source
£1.43B
Total GDPR fines issued in Europe from Jan 2022 – Jan 2023
View Source
83%
of UK businesses reported repeated data breaches
View Source
£4.03M
the average total cost of a supply chain compromise was
View Source
Breach Mitigation
60%
of breaches were discovered within days based on analysis of 79,000 breaches in 88 countries
View Source
Breach Prevention
64%
of businesses do not have some form of cyber insurance
View Source
87%
of businesses have not reviewed the risks posed by their supply chain
View Source
51%
of UK businesses do not have a formal cybersecurity strategy in place
View Source
Sectors most at risk
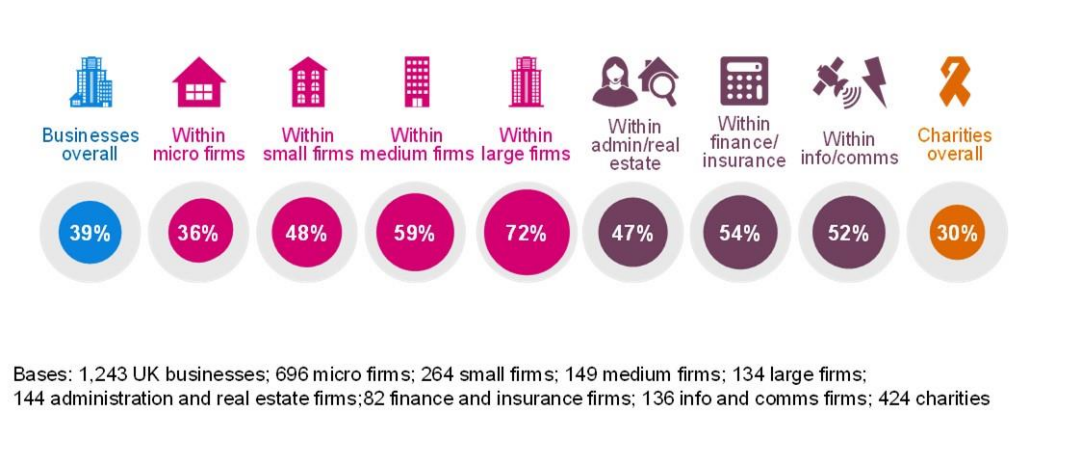
Across all organisations (i.e. not just those identifying breaches or attacks), medium and large businesses are more likely to experience a cyber crime than smaller ones. Similarly, high-income charities (25% of those with an income of £500,000 or more, vs. 8% of all charities) are also significantly more likely to have experienced a cyber crime. This reflects the pattern for all cyber security breaches and attacks more generally, as described in Chapter 4. As this series of reports has previously noted with regards to all breaches and attacks, this difference may to some extent indicate underreporting in smaller organisations, which tend to have less sophisticated cyber security monitoring in place.
In terms of sector, professional, scientific and technical businesses are more likely than others to have identified cyber crimes.
Types of cyber crime
| Type of cyber crime |
Businesses |
Charities |
| Phishing attacks |
89% |
85% |
| Viruses, spyware or malware |
12% |
7% |
| Hacking (unauthorised access or online takeovers) |
7% |
8% |
| Ransomware |
4% |
4% |
| Denial of service attacks |
2% |
1% |
Bases: 346 businesses that identified a cyber crime in the last 12 months; 172 charities
View Source
Understanding Cybersecurity Threats
Overview of Common Cyber Threats
In 2024, UK businesses should remain vigilant against a range of prevalent cyber attacks. Some of the most common types they should be aware of include:
Ransomware Attacks: Continuously evolving and highly damaging, ransomware attacks encrypt critical data, rendering it inaccessible until a ransom is paid. These attacks can paralyse operations and lead to substantial financial losses.
Phishing Attacks: Phishing remains a persistent threat, with increasingly sophisticated tactics aimed at tricking employees into divulging sensitive information or providing access to corporate networks. Spear phishing, where attacks are personalised and highly targeted, is a currently prevalent form of phishing to look out for.
Supply Chain Attacks: Targeting interconnected networks through third-party vendors or weak links within the supply chain, these attacks can infiltrate multiple businesses simultaneously, causing widespread disruptions.
IoT Exploitation: With the proliferation of Internet of Things devices, cybercriminals exploit vulnerabilities in these interconnected devices to gain access to networks or launch attacks, potentially compromising sensitive data or disrupting operations.
Credential Stuffing and Password Attacks: Cybercriminals leverage stolen credentials obtained from data breaches to infiltrate systems by using automated tools that try numerous username-password combinations, exploiting reused or weak passwords.
Man-in-the-Middle (MitM) Attacks: These attacks intercept communication between two parties, allowing threat actors to eavesdrop, modify, or steal sensitive information exchanged between them.
AI-Driven Attacks: With the convergence of AI and cybersecurity, there's a rising concern about the potential for AI-driven attacks, where automated systems exploit vulnerabilities, launch targeted attacks, or create more sophisticated malware.
Business Email Compromise (BEC): BEC attacks involve impersonating executives or trusted partners to trick employees into transferring funds or sensitive data, leading to financial losses or data breaches.
Insider Threats: Whether intentional or accidental, insider threats from employees or contractors pose a risk through unauthorised access, data theft, or inadvertent actions that compromise security.
These are just some of the many different attack types that are making the rounds. As new technologies continue to evolve, you can be sure that more will follow.
Five key stages of cybersecurity
Cybersecurity is a circular process that constantly repeats to stay up to date with the latest technology developments and threats. It involves several stages:
- Identify
Security begins by understanding your IT infrastructure and applications, and the information that they support. This is also the time to identify the cybersecurity risks facing your organisation.
- An external assessment is often invaluable in identifying weaknesses and poor security practices.
- Auditing tools will help you gain full knowledge of all systems and applications within the business. Often a good starting point would be an internal Pen test.
- Protect
Only then can you put protective measures in place to defend them against cybersecurity threats.
- Time to layer up – Complex password policies, MFA for all users for any cloud-based applications and VPN connections. Email Security to reduce SPAM and malicious emails, Remove those Global admin rights from standard accounts! Patching of firewalls, switches, Wi-Fi as well and Server, Desktops for both OS and 3rd party software. All of the above can be overwhelming for small IT teams and that is where outsourced managed services are very effective in helping with workload and filling in gaps in key skills.
- Check what you get as part of your MS365 licensing and look at additional MS365 features such as conditional access and Microsoft labels to add further protection to both your users and data.
- Ensure you have an air gapped backup of your data - You have two options when hit with Ransomware, pay the Ransom or rebuild and restore your data from backup. If your backup is not working or destroyed as part of the attack then you are out of options.
- Train your staff on Cyber Security – The human firewall is normally the weakest part of any system so training is essential to help users identify and fend off and report attacks.
- Check your Cyber insurance policy to make sure that you comply with all stipulated technical requirements.
- Detect
Many online attackers are adept at flying under the radar. Proper network and system monitoring is crucial if you are to spot them.
Have routines and processes in place to check alerts for suspicious activity both on prem and in cloud tenancies or invest in a SIEM such as Microsoft Sentinel which can help identify suspicious alerts and attacks. Don’t forget to and respond to any alerts from your AV.
- Respond
A proper cybersecurity plan acknowledges that attacks may succeed despite your best efforts. Just as you should have a plan in place for disasters like fires and floods at home, an incident response plan for cybersecurity attacks will help you hit the ground running and minimise the impact of an attack.
- 81% of customers surveyed don’t have a valid DR plan to deal with a major Cyber incident – putting together a recovery playbook is an essential part of an efficient plan. The plan will help map out all systems and more importantly identify key systems that need to be brought online first. Most response’s will require 3rd party assistance and they will need direction with regards to priorities as they wont be close enough to the business to make the decisions themselves.
- Don’t forget about the non-technical aspects of any response. Data breaches need to be reported and legal and PR teams will need to be engaged. Just remember that you cannot buy back reputation.
- Recover
Should the worst happen, it’s important to have backups in place to get up and running quickly again. Smart businesses also learn from attacks so that they can harden their security posture.
If you are hit with Ransomware and your data has been encrypted you are left with two options, Recover from Backup or pay the Ransom. If your backup has been compromised as part of the attack or is inadequate then you are out of options.
Once again time to check the terms and conditions of your cyber insurance as you may have to wipe and rebuild all systems as a condition of the policy paying out. Any backups will need to be checked and the data sanitised before it can be restored. Simply restoring whole backups may lead to back doors being restored and your network being encrypted again.
The amount of work that goes into recovering is often underestimated and the long term recovery can still be ongoing for months after the incident.
Then comes the only real positive outcome of any cyber attack: learning. Conduct a post-mortem, analysing your system logs to understand how the attackers exploited your weaknesses. Use these insights to enhance your security policies and make any necessary changes to your infrastructure. What doesn’t kill you makes you stronger.
A robust incident response plan includes information such as a contact list, an escalation process, and a flowchart to manage the whole problem from start to finish. As with all other measures outlined in this guide, investing some time and effort in getting this right now will save you countless headaches later.
Even if you don’t have lots of in-house skills and resources, you can still improve your cybersecurity stance with some thoughtful planning. Taking the time to understand the cybersecurity challenges facing your business and the options for mitigating them will reassure you and your customers that you’re competent and capable in managing their sensitive data.
Don’t be discouraged by these five steps. They may seem daunting but much of the work involves some simple and straightforward cybersecurity practices. For more information, the UK Government’s Cyber Essentials Scheme mentioned above is a good place to start.
Do implementing security measures and pursuing innovation have to be mutually exclusive? Here, Rich Nelson outlines how businesses can strike the right balance and ensure they are staying safe – and staying ahead of their competition:
Emerging Threats in 2024
In 2024, emerging cybersecurity threats in the UK present a multifaceted landscape, demanding heightened vigilance and strategic preparedness from businesses across industries. Among these threats are:
AI and Machine Learning Threats: The convergence of artificial intelligence (AI) and cybersecurity has created a new frontier of threats. Malicious use of AI algorithms can automate and enhance cyber attacks, enabling sophisticated phishing attempts, creating highly convincing deepfake content for social engineering, or optimising malware to evade traditional detection methods. These AI-driven threats have the potential to rapidly adapt, learn, and autonomously execute attacks, challenging conventional cybersecurity defences.
Learn more about the ways in which AI is used to launch sophisticated cyberattacks and invaluable strategies for organisations to protect themselves from these evolving threats in Lindsay Thorburn’s presentation from Cyber Security Expo:
IoT Vulnerabilities:
The proliferation of Internet of Things (IoT) devices continues to expand the attack surface for cybercriminals. Vulnerabilities within interconnected IoT ecosystems pose significant risks, allowing threat actors to exploit devices and networks for unauthorized access, data breaches, or launching large-scale distributed denial-of-service (DDoS) attacks. Inadequately secured IoT devices, from smart home gadgets to industrial systems, present potential gateways for cyber intrusions, demanding robust security protocols and continuous monitoring.
Supply Chain Risks:
The interconnected nature of modern supply chains introduces vulnerabilities that adversaries can exploit. Threat actors target suppliers, third-party vendors, or weak links within the supply chain to infiltrate networks, implant malware, or compromise the integrity of products or services. These attacks, often highly sophisticated and far-reaching, can disrupt operations across multiple entities simultaneously, leading to widespread economic and reputational damages.
Understand the significance of documenting and mapping your supply chain to improve organisational resilience, incident management, and business continuity planning with Matthew Goodbun’s deep dive into supply chain risk:
Dive into our guide on supply chain security for further insights, practical strategies and protective measures:
In response to these emerging threats, UK businesses must adopt a proactive and multifaceted approach to cybersecurity. Implementing AI-powered threat detection and mitigation solutions becomes imperative to counter AI-driven threats. Securing IoT devices through robust authentication, encryption, and regular updates is crucial, alongside implementing network segmentation to contain potential breaches. Furthermore, ensuring supply chain resilience involves rigorous vetting of vendors, enforcing stringent security protocols, and establishing contingency plans to minimise the impact of supply chain disruptions.
To navigate the evolving threat landscape, collaboration among businesses, government bodies, and cybersecurity experts remains pivotal. Continuous monitoring, threat intelligence sharing, and investing in cutting-edge technologies and skilled personnel stand as essential pillars in fortifying defences against these emerging cybersecurity threats in 2024.
Risk Assessment and Management
Identifying Business Assets:
The first step in cybersecurity risk assessment is identifying and catalogue
Risk assessments involve identifying potential threats and vulnerabilities that could impact these assets. It includes evaluating the likelihood of a threat occurring and the potential impact if it materialises. This process often involves techniques like vulnerability scanning, penetration testing, and analysis of historical data breaches to understand potential risks.
In a recent study, our technical consultant conducted an extensive cybersecurity risk assessment across more than 100 small and medium-sized organisations, shedding light on their current cybersecurity preparedness and potential areas of improvement. Watch Mark Lomas present his take on these findings and the actions you need to take today:
Implementing Risk Mitigation Strategies:
Once risks are identified and prioritised, businesses need to implement strategies to mitigate these risks effectively. This could involve a variety of measures such as:
- Security Controls Implementation: Deploying firewalls, encryption, access controls, and other technical measures to protect against specific threats.
- Policies and Procedures: Establishing and enforcing security policies and procedures, including employee training on cybersecurity best practices, incident response plans, and data handling protocols.
- Regular Monitoring and Updates: Continuously monitoring systems for potential vulnerabilities, staying updated with security patches, and conducting periodic audits and assessments to ensure ongoing security.
For UK businesses, aligning these practices with frameworks like the National Cyber Security Centre (NCSC) guidance, Cyber Essentials, or ISO 27001 standards can provide structured approaches to managing cybersecurity risks effectively. Moreover, compliance with regulations like GDPR necessitates a robust risk management approach to safeguard personal data.
GDPR and Data Protection Laws:
The General Data Protection Regulation (GDPR) is a comprehensive data privacy regulation that governs the collection, processing, and storage of personal data of individuals within the European Union (EU). Even after Brexit, the UK has retained GDPR principles through its own UK GDPR, aligning closely with the EU GDPR. It imposes strict requirements on businesses regarding consent, data breach notification, and the rights of individuals over their data, and delivers penalties of up to 20M euros or 4% of your annual global turnover (whichever is higher) for breaches.
NIS Directive:
The Network and Information Systems (NIS) Directive is aimed at ensuring the security of essential services (e.g., energy, healthcare, transport) and digital service providers. It mandates cybersecurity measures and incident reporting for operators of essential services and certain digital service providers within the EU, promoting a higher level of cybersecurity preparedness and resilience.
Cyber Essentials:
Cyber Essentials is a UK government-backed scheme designed to help businesses protect themselves against common cyber threats. It provides a baseline of cybersecurity measures that organisations can implement to demonstrate their commitment to cybersecurity. Cyber Essentials certification is increasingly becoming a requirement for bidding on government contracts and is seen as a valuable step in improving overall cybersecurity posture.
Regular reviews and updates to risk assessments are crucial as the threat landscape evolves rapidly. By consistently reassessing risks and adapting mitigation strategies accordingly, businesses can better protect themselves against cyber threats and ensure the resilience of their operations.
You can claim a free* cyber security risk assessment with our specialist team of technical consultants, who will discuss and identify potential areas of risk within your business and offer tailored advice and a board level report documenting the risk level of each key area of attack.
Different types of security solution
Cybersecurity for businesses hinges on three pillars: technology, process, and people. Technology fortifies systems; processes establish frameworks for risk mitigation, and people, through training and awareness, serve as the human defence. Getting these layers right is key.
Technology
This list is by no means exhaustive, but covers some of the most common cybersecurity technologies available.
Firewall
Firewalls act as the guardians of your network, preventing unauthorised external access to internal resources while allowing authorised users. A variant, the web application firewall, safeguards web applications by scrutinising visitor traffic, effectively filtering out potential hacking attempts.
Endpoint detection and response
PCs, tablets, and mobile devices pose significant vulnerabilities for businesses. A single compromised device can serve as an entry point for an attack. Centralised management is crucial to allow only securely protected devices into your systems. This solution is critical for any organisation with a bring-your-own device (BYOD) policy. Going one step further, an EDR system identifies suspicious activities or software on endpoints and takes necessary actions, including isolating them when needed.
Secure cloud storage
If your organisation utilises cloud storage for data, don't presume it's automatically private or secure. Secure account storage measures are vital to safeguard your valuable information. Consider leveraging a Cloud Access Security Broker (CASB) for encrypting cloud data, thwarting potential access by hackers to sensitive customer information.
DRaaS
Ransomware poses a severe threat to critical business files. Safeguard them by backing up onto a secure external medium, ideally off-site, shielding them from potential risks like fire or floods. Consider Disaster Recovery as a Service (DRaaS) via cloud-based backup and restoration. This service ensures dependable data backups in robust data centres, simplifying backup management for a straightforward monthly fee.
Explore the methodology and approach to cementing your backup and recovery programme in our ultimate guide to Backup and Disaster Recovery:
Mail security
Email is more than 40 years old, and in its common form is still one of the most insecure communications mechanisms. Using secure protocols such as Secure/ Multipurpose Internet Mail Extensions (S/MIME), you can encrypt your communications and digitally sign your emails to avoid imposters. Other technologies to help secure your email include the Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting and Conformance (DMARC), all of which combine to stop phishing and email spoofing attacks.
Virtual Private Network
Firewalls are one part of the secure access solution. Another is a Virtual Private Network (VPN) system, encrypting traffic to and from a remote worker’s device, ensuring secure access to office applications. VPNs also verify the legitimacy of the remote device, preventing unauthorised access to internal resources by potential imposters.
Data encryption
Data encryption is a foundational principle in cybersecurity. By encrypting your data during both storage and transmission, you can stop attackers from understanding it even if they get hold of it. The key here is to manage your encryption keys properly so that unauthorised people can’t unlock your information. This takes expert help.
Malware detection
Worms, ransomware, and viruses can all lay waste to your IT infrastructure. Advanced malware detection tools can scan multiple weak spots for suspicious software. Use them to check incoming emails and attachments, monitor the websites that employees visit, and scan existing files stored in your organisation.
IDS/PS
Smart companies don’t just guard the perimeter of the network against attackers; they also watch for attacks inside the network. An intrusion detection and prevention system identifies potential threats, such as malware or unauthorised access attempts, through real-time monitoring and analysis of network traffic or system behaviour. While intrusion detection identifies and alerts about these threats, intrusion prevention systems take immediate action to block or mitigate the risks.
IAM
One of the most dangerous forms of attack is account hijacking, in which attackers take over an employee’s system account. IAM helps prevent this, while also ensuring the right individuals have the appropriate access to data, applications, and networks. It involves creating, managing, and revoking user identities, defining user roles, enforcing access policies, and monitoring user activities to enhance security and compliance.
Multi-factor Authentication (MFA) is an additional layer of security that requires users to provide multiple forms of verification to access accounts or systems. Typically, beyond a username and password, MFA prompts users to enter a unique code sent to their mobile device, use biometric authentication (fingerprint, facial recognition), or utilise hardware tokens. MFA significantly strengthens security by adding multiple authentication factors, reducing the risk of unauthorized access even if passwords are compromised. Together, IAM and MFA play pivotal roles in fortifying cybersecurity defences by controlling access and ensuring only authorised individuals gain entry to sensitive systems and data.
Zero-trust architectures
Firewalls and VPNs are useful for protecting your network perimeter, but what happens when that perimeter no longer exists? The pandemic sent large numbers of employees home, and remote work is now a fact of life. That means companies aren’t sure what devices people are using to log into their systems, or which networks they’re on. Zero-trust security is a response to that. It verifies people using strong identity checks rather than relying on their devices. It also protects individual computing assets such as files and applications rather than granting people complete access to everything. Gartner has advised people to move away from VPNs as a solution in favour of zero-trust architectures, but this is a big undertaking with many moving parts.
SIEMs
One of the biggest challenges for security teams is gaining visibility into all of the security events on their network. A Security Information and Event Management (SIEM) system logs and correlates these events, providing a clearer picture of what’s happening across the infrastructure. Security teams can use it to spot emerging trends and get a clearer picture of what’s happening over time.
Process
Data classification
It’s difficult to protect your data if you don’t know who owns it, what it is used for, or how sensitive it is. Data classification tags your documents at the point of creation and can also discover existing files, so that you categorise them en masse. This makes it easier to store data with the appropriate level of security and apply different management policies to protect your information.
Patch management
Unpatched software is a common vulnerability that hackers can exploit. It is important for businesses to update their applications and operating systems with the latest security fixes. System management and patch management tools can help apply these fixes quickly with minimal fuss by automating the key steps.
Vulnerability assessments
Vulnerability assessment is an important part of your risk identification process. It analyses your IT infrastructure, finding potential weak spots for you to plug. There are dedicated tools to help with this step that automatically discover and classify the software and hardware assets within your organisation, searching lists for known vulnerabilities.
Penetration testing
There is nothing better than a second set of eyes. A penetration testing consultancy, also known as an ethical hacker, will try to break into your IT infrastructure, documenting everything that it finds along the way. The result is a report highlighting your weaknesses so that you can harden them against real attacks.
Chains of command
Examine your core business processes, such as issuing payments, granting access to senior executives, and managing physical building security. Identify gaps that attackers can exploit and use strict procedures to close them. For example, don’t allow a single person to make significant payments. Involve two people and implement a set of checks and callbacks before authorising financial transactions.
People
Employee training and awareness stand as integral components of a robust cybersecurity strategy for businesses. Recognising the pivotal role employees play in the security posture of an organisation, ongoing education becomes paramount. The importance of employee education lies in empowering staff members with the knowledge, skills, and awareness necessary to identify, mitigate, and report potential cyber threats. By instilling a culture of vigilance and responsibility, businesses can significantly reduce the risks associated with human error, which often serve as gateways for cyber attacks.
Training
Regular training modules serve as the cornerstone of fostering a cyber-aware workforce. These modules should encompass a diverse range of topics, including best practices for password management, recognising phishing attempts, identifying suspicious links or emails, and adhering to company security policies. By providing frequent and targeted training sessions, businesses can ensure that employees remain updated on the latest cyber threats and preventive measures, thereby reinforcing a proactive stance against evolving risks.
Simulation exercises
Simulated phishing exercises represent a proactive and hands-on approach to enhancing employee readiness. By simulating real-life phishing scenarios, these exercises test employees' ability to discern phishing attempts, educate them on common tactics used by cybercriminals, and cultivate a cautious mindset when interacting with digital communications. These drills not only serve as educational tools but also act as diagnostic measures, enabling businesses to identify areas that may require further training or reinforcement. Ultimately, such exercises empower employees to become the first line of defence against cyber threats, fostering a more resilient and security-conscious organisational culture.
Security policies
Every business needs a robust and comprehensive security policy, covering how employees and visitors should use resources such as devices, applications, email, and networks. This should also extend to other less obvious areas such as how they dispose of paper. A clean desk policy, for example, encourages more than just a tidy workplace — it also stops sensitive information from falling into the wrong hands.
BYOD policies
Creating a secure work environment entails establishing robust policies and measures that adapt to the evolving nature of work, especially in an era where flexibility and remote operations are prevalent. Implementing Bring Your Own Device (BYOD) policies forms a crucial aspect of this strategy. These policies delineate guidelines and security protocols for employees using personal devices for work purposes, balancing convenience with stringent security measures. By outlining device requirements, encryption standards, and access controls, businesses can mitigate the risks associated with potential vulnerabilities on personal devices while maintaining productivity and flexibility.
Conclusion
Cybersecurity is not an ‘add on’ and must be embedded in your processes and culture. Targeted investment requires a careful assessment of your organisation’s current and future needs and capabilities. The majority of breaches are caused by failures on the part of people and processes. Therefore, when it comes to investment, training and awareness are equally as important as the latest technical solutions.
View Source
Resources
These resources encompass guidance, tools, certifications, and communities aimed at enhancing cybersecurity practices and resilience for UK businesses across various industries.
Provides guidance, alerts, and resources for cybersecurity best practices and incident response tailored to UK businesses.
Provides guidance on data protection and compliance with GDPR regulations, offering resources and tools specifically for UK businesses.
Offers advice and resources to help businesses and individuals protect against online threats, including guidance on cybercrime and safe practices.
Provides a platform for networking, sharing best practices, and accessing cybersecurity resources specifically tailored for UK businesses.
Facilitates collaboration and information sharing on cyber threats and vulnerabilities among businesses, government, and cybersecurity experts.
Protect Your Business with our Expert Cyber Security Solutions
Safeguard your organisation against evolving cyber threats with Probrand's comprehensive cyber security services. From threat detection to robust defences, we’ve got you covered.
See More